|
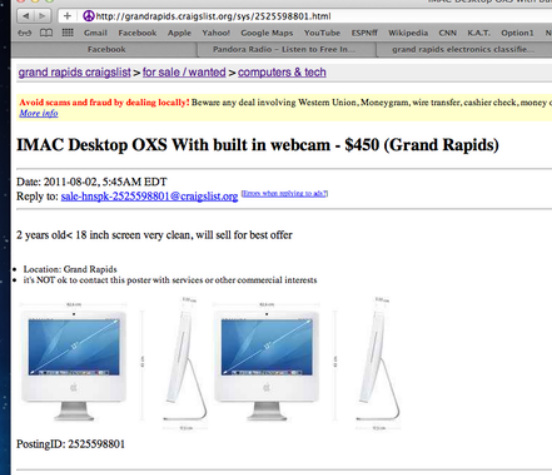
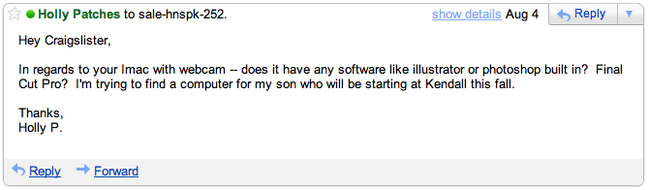
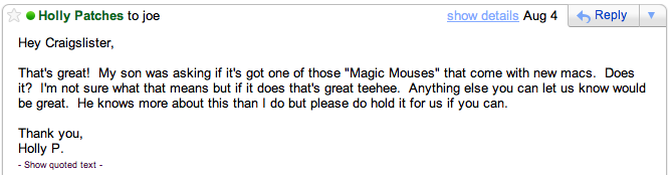
Ok...this may take a little while. If you just want to here about the recovery mission you can scroll down until you see the header "Mission MacRecovery". Also - even though this is long and will probably be edited and added to over time, there is still so many other fun details that just didn't make the cut. It was quite the adventure. In early 2011, Jenny and I moved into the lower level of a duplex in the West Side of Grand Rapids. It seemed to be a great find. It was overall "nice", roomy, close to my work/downtown and, what I thought was an awesome bonus, it was directly across from a park. We wouldn't be stuck in the middle of a neighborhood where the variable of neighbors determine your general feelings of safety and hospitality, but instead we'd walk out our front porch and have nature -- a pleasant, wooded park. That changed as summer 2011 hit and three (chained up) benches showed up about 10 feet into the park, directly across from our house. For 3 months Jenny and I were bystanders to LARPing, chanting and what seemed to be about 3 different "groups" of people that constantly congregated at or around the benches directly across from our house. All this was of little consequence but what made us uneasy was the fact that when we left our house, there would always be people sitting on the benches looking directly at us. This led Jenny and I to say things like "the next time we have people over we should move those benches further into the park" but it was hardly a priority. That was, until August 19th. On August 19th, with Jenny already off to work for the evening, I left the house around 6:30pm to do three hours of work at a radio station and returned home around 9:30pm. As I put my key in the door, I noticed Jenny's bike had fallen over. My heart didn't skip a beat until I opened the door, my eyes gazed up from the bike only to see my computer desk to be void of my computer among other things. To this my reaction was a loud, resounding "FUUUUUCK!" that people later reported hearing. After storming around the house, accounting for as much of the lost items that I could, calling the police and angrily walking over to the "bench people" that happened to be there at the moment with what people have described as "crazy eyes" asked them 'how long they had been there' among other things. Eventually the police showed up, wrote down some stuff and actually dusted for prints but, long story short, nothing of any consequence ever came of that. Later that night though, a number of facts were burning in my head: I was only gone for three hours. It was only 9:30pm and still light out when I returned home. I had left and returned from work on my bicycle with my car parked in front of our place in the street. These facts not only point to the idea of being surveilled but, given our circumstance, it felt more than obvious it was a "bench person". Given that conclusion, I did heavy "surveilling" of my own over the next few days. Due to my worries about the legality of my practices, I'll leave it at that, but, once again, long story short, nothing of any consequence ever came of that. From here, aside from Jenny and I walking around the neighborhood with my iPad hoping to stumble across our wifi network (we have internet through the burgeoning technology of WiMax that allows our wifi unit to operate anywhere in the Grand Rapids area), weeks went by where I could do little more than watch Craiglist and slowly face the idea that life would indeed go on -- but I was certainly "dragging my feet" mentally on that notion (Give me a break - we didn't even know about rentals insurance, let alone have it when it happened). Calling the detective assigned to my case did nothing more than shut another door on my hopes of catching the person who did this...someone that could easily be sitting in the park, still watching us that day. Then, on August 4th, more than two weeks since the break in, I went to work once again for only a few hours. While there "Board op'ing" I had time to check out Craigslist for the first time in a few days. While searching, a post by someone selling an iMac, using a stock-photo, being very nondescript and at the very least, lying about the age of the computer, caught my attention. This was only the third time I'd suspected a post enough to take the time to send an email from my alias email account. That email went a little something like this: Obviously I was fishing for the exact programs I had on my computer. If you do not know, all three of those programs are not standard to a mac. Photoshop and Illustrator may be a bit more common but Final Cut Pro is a professional video editing software that is fairly expensive. So when he fired back with: I was obviously ecstatic. Actually, I was much more than ecstatic - I felt vindicated. Even though it may not seem like much, as far as I was concerned, this is someone who is clearly not tech savvy given the way he's writing about the computer (so why is he selling it? Why would he have it?) and he just confirmed it indeed has Final Cut Pro on it, though he didn't say it in a way to give me confidence. That's why I responded with: I regretted this email within the hour I sent it. This one didn't scare him off luckily, but it feels like I went for something a little too specific. I don't indeed have a "magic mouse" but I did have a weird, tiny laptop mouse. I was afraid I fished too much but alas he responded with "Ok ill hold it for u, just let me know when ur ready to purchase". From here, I tried to involve the detective. After talking to her on the phone she seemed to agree their was a good chance this was my computer and instructed me to get him phone number. He wanted ours. So began his shiftiness and the detectives specifics which only made me more adamant he was dealing with a "hot" product but also the problem that led me to make a second alias email to start contacting him with as well. In the next few days he made comments like "I just want to make sure I can trust u" which once again, only made me more confident he had my computer. But, due to the rigidness of how the detective would work with me, not to mention, him -- he eventually stopped contacted Holly P. out of suspicion. This is where my second email of "djjunk6823" luckily came into play. I was getting so scared that he sold it due to his not responding to Holly (and it had almost been two full weeks at this point), that, out of desperation, I sent him an email giving him my phone number with my second alias email. This correspondence had only gone back and forth once and was the polar opposite of what he had experienced with Holly -- and it worked. He called me within 2 days. He seemed to be vetting me by asking what I wanted it for. At this point I made sure not to ask anything too specific - and when he filled me in about what "Garageband" was, I sounded sincerely impressed. By the end of the phone conversation he had admitted he didn't know much about the computer having "gotten from his sister a few weeks ago" and he gave me an address he wanted to meet at later that day. As soon as I hung up the phone, I rushed over to the computer, put the address into google maps and YUP! The address was about 4 blocks from my house! The park across the street is the closest park in the area! Out of all of Grand Rapids, he wanted to meet at a house just four blocks from where I live?!?! BAHAHA got him is what I was assuming. I immediately called the detective to inform her of the even higher pile of circumstantial evidence. At this point, the trend has to be impossible to ignore -- they just need to go check it out for me (as she once said she could) and then take it. But apparently, it wasn't that easy. It was only at this point, even with an address that's around the corner, the confirmation he's given me about programs, the use of stock photos, the shiftiness in details and meet up times, his lack of knowledge and admitted recent acquisition of the computer, that she told me "we can't do anything without the serial number". Side-note: I was really hoping I wouldn't have to do it myself because if it was indeed my computer it would have my face all over it or if he was indeed the guy that stole it he saw us go in and out of our house every day. Basically, if he recognized me before I even got a look at it, I risked having him not even answer the door. To make a long conversation short, by the end of it I said to her "So you're telling me that I have to get someone who is willing to go look at it for me and when they confirm it's mine, their only course of action is to TAKE IT?" She said yes. At the very least she was able to tell us that that was indeed his house, that he was 18 and that she had only dealt with him in situations where he was the victim. Knowing anything extra, let alone all that, made the random meeting with him that much more reasonable seeming. Operation MacRecovery: T-minus 5 hours until the Craigslist guy calls "DJjunk" to meet up with him: Well, with that, I had no other choice but to see how awesome my friends were. One hour and a few awkward phone calls later, I had enlisted the perfect friend for the job and an equally willing and ballsy team-mate. My front-man who had the time for details recently returned from Marine training and all his life he has been that guy who's confidence and cockiness should have gotten him in a ton of trouble, but somehow it's always worked to his advantage. A lot. Having him on my side felt like bringing Super-man to a tug-of-war. I have only heard tales of what it's like when guy number 2 "rages out", but it was only helpful given the circumstances. Sidenote: Both guys, when I offered them money, replied with something to the effect of "What? I'd pay you to do something like this." Also, from this point on, I will refer to guy #1 by the actual alias he had to go by: Monroe. I didn't pick the name attached to the email assuming I'd be having a white 20 something meeting up with him using it. We'll call Guy #2 - the guy playing strong and quite back-up - will be referred to as Nick. Luckily, I had laid in bed the night before basically imagining every scenario that could play out if the craigslist guy called me. As soon as I picked up my main operative we went to my place of employment and I started outlining what he should look for to tell if it's my computer. From physical scratches, to which kind of mouse, to the registration name of certain programs, to restarting the computer to see if my name pops up -- we had it all covered. I would be listening remotely by having an open cell-phone in their pocket just in case anything went wrong. There was also talk of putting an audio recorder in his pocket but Michigan law seems messy on that topic... T-minus 3 hours until phone call: We go and get a few beers in Monroe for two reasons: he might as well have a little more courage and we have everything planned a few hours too early... T-minus 1 hour until phone call should happen: Nick meets up with us at our bunker. He gets most of the details of what to look for as well as a recap of the plan of attack/conversation tactics, etc. The hour he is supposed to call: Longest hour of my life. He didn't call. 15 minutes later: I call him. Luckily he answers (given how other communications and plans have gone between him and Holly P. it seemed like there was a good chance this wasn't going to happen). He says he's just running late and he'll be to his place in about 20 minutes. For expediency purposes, I had the excuse of "wanting to put my kid to bed later" so I was hoping to meet him at his place in 20 minutes. 25 minutes later: Monroe and Nick jump in a car to drive a mere 3 blocks, acting like it took them 20 minutes to get there. As they pull up, they drive past a house with about 5 guys sitting on the porch just four houses down from the house they are meeting him at. To this, on of the guys says something like "Gha - glad we're not going there". After they park they go and knock on the door only to have a mom answer. Not exactly what we were hoping for but not nearly the worst thing. Her first question was "Are you guys from the Christian Youth Group?" To this, my friends showed off their add libbing skills with a quick story of them "...being from...uh...something else." To their credit, they knew they didn't want to tell the mom about the computer in the off chance she didn't know of it either, and that would possibly screw up the entire operation. So, after one more awkward comment or so, they return to their car to talk loudly so I could hear them through the phone in their pocket. About 45 minutes and a group of 12 year old girls dancing around their car later - it's just late enough for it to really be dark outside: He finally shows up. I'm listening through the phone in their pocket as the guys proceed to walk for what seems like a very long time. After hearing them walk past what sounds like a group of people and then hearing a dog or two, I lose the connection. My surveillance to make sure everything is going alright and having the option to call the police just went dead. Sitting at our remote location no longer did us (Jenny and I) any good - so we did the only thing we could do; we just in our car and went and sat outside the house they presumably just went into. What's really going on: After he came up to them, he said he had the computer at his uncles house and it was just down the street. They continue to walk back down the street and walk directly into the house with 5 or so older guys sitting on the porch. To state the obvious -- this was not the type of situation we -- really they -- were hoping for. One minute later they find themselves on the second story of the heavily resided house. Their were 2 or 3 more people in the house but it does seem like a family situation. Some dogs are freely roaming around them, Nick spends most of his time petting and playing "snuggles" with the pups to pass the awkward moments between questions. But their they are -- face to face with the iMac they came to investigate. When they get to it, it's already running. It's signed in under an unfamiliar user name but the physical scuff on the front that I told them to look for is there -- poorly recalled by me, but it's there none-the-less. At that point, Nick asks about the USB connection on the back for the sole purpose of looking for the second scuff I told them to look for - it's there. Between those and the fact that the exact mouse and keyboard I had are attached to this computer it seems crazy that they didn't just immediately feel confident it was mine. But the thing is, they didn't necessarily need to convince themselves at this point - though a little more concrete evidence would be nice - but they'd need to convince him that they know everything about what's going on here. So they look over the computer for a few minutes -- they open a program I told them would be registered to my name. When it opens, it does not show my name. With this, they glanced at each other and a crack has formed in there assuredness. But they continue on to some of the other plot points that were discussed. Luckily, the idea of getting him to reset the computer in the event it was already on when they got their was discussed. They asked to see "how well it booted up". He obliged. It takes about 20 seconds to reboot but then the account screen shoots up. From their perspective he seems to attempt to sign in as quickly as possible but there it was: my name at the top of the account list. Monroe attempts to push delete before he hits enter to send in his password because he was locked and loaded with our secret weapon - he knew the password to my account. If there was one way to send the message that he should not be in possession of this computer, it would have been to enter the password to the locked account -- but that moment had just passed. From here - as Monroe collects his thoughts on how to start the real conversation, the kid is grasping for things to say about the computer amidst the silence. As he's stating something vapid, Monroe cuts the kid off in mid sentence: "Here's my biggest question...Chad Becker is one of my good friends and his computer is in your house right now." The kid replies with a simple "What?" "My friend, his computer...it's on your computer desk right now." From here the exact conversation gets hazy but it goes from the 18 year old kid acting like "that's crazy that this is a stolen computer" and within a few exchanges says something like "Well...uhhh...technically it's mine now though." Monroe: "No. It's not." For a bit the kid is putting up a fight realizing that they are expecting to leave with the computer but at that point says one of our pre-planned conversation points of: "Look, I can get the cops involved if you want - but it would be a lot easier if we just leave with this computer right now -- I am wearing a wire." *While saying that last part, Monroe lifts up his shirt slightly to reveal the random, disconnected piece of wire we taped to his stomach just in case he felt the need to freak the kid out. From that point on, the kid gets a lot more apologetic and understanding. They start to shut down the computer and wrap it up as they discuss what else they took during the break-in but for the most part keeping it light with niceties like "Yeah man, we don't know what exactly happened -- we understand you're likely just a middle man -- but we're leaving with this computer." The kid oddly enough, walks to computer to the door at which point Nick takes it from his hands and they continue to walk outside to the porch full of people. One of them chimes in with 'that's a nice computer' to which Nate said 'yup' without skipping a step. They are walking out to their car and once again, oddly enough, with the kid in tow. During this short walk, the kid is freaking out about the files on his side of the computer. He asks "hey can you guys delete my stuff." To this, Monroe replies, "yeah, we just need the password". The kid, astounding me a third time in this story, responds with "I'll text it to you." Then, with one more 'sorry' from the kid, they quickly jump in to the car and drive off as quickly as possible. Back to my perspective and rewind 1 minute: Me to Jenny "Someone's walking up to Nick's car -- it's Nick and Monroe! Do they have the computer? Holy shit - they have the computer! Is there a third guy there? Wait, what? Someone walked them to the car? Someone walked them to the car. Holy shit they have my computer!". And then we flee in our vehicle as they do. Post-game: I'm not sure if it's to his credit or to his stupidity but the kid did in fact text us the password. To make another long story short, he does have some things that would be pretty embarrassing to edit together and put out on the internet, but that's not a reasonable course of action given the current state of the situation. Further details will need to be inquired about with me directly as I'm not sure how much I should put out on the web given the ongoing investigation and whatnot. Hell, even this is probably highly frowned upon...oh well; I was getting really sick of telling this story.
CHIA! Please leave a comment or request for parts I may have glossed over. This took a long time to write and I imagine we will be adding to it as we discuss things.
0 Comments
|
Immense thanks to "Monroe" and "Nick". I would probably still just be a bitter victim without you guys. |